Saturday, April 21, 2007
My Last Post on Security Stuffs
To all my dereast and loyal readers, i am sad to say that this might be the last post i make regarding network security or web security here. Why? Because i am off to something even more exciting and challenging. These 2 months of blogging had been really great with a vast amount of knowledge exchanged from the community. Its a short yet fruitful journey for me and thank you guys for all the support and emails you gave me. I can only say sorry here because i will not have the time to actually blog too much on security again. Instead something big and exciting is waiting ahead for me to accomplished. Nevertheless, you guys can still email me regarding security issues you have. I will try to response fast. Once again, thank you.
Wednesday, April 18, 2007
Windows Vista Forensics
I was reading articles and i happen to stumble a microsoft vista forensics article. In this article, Jamie Morris from Forensic Focus share his view on vista forensics and several new vista features. I think microsoft is really picking up on security these days compared to the past and their response to security incident is fast. Yes, you can agrue that vista is hacked and it is not secure, but still which softwre doesnt have bugs? Most importantly, they always release patches fast after certain exploits has been discovered and allowing end users like us to do update. Linux is powerful and has improved a lot over the years, but still i would prefer to use microsoft as my main OS and Linux as a VMWare image, why? Because i think Bill Gates is great. I give full support to this man 100%. Without Bill, you wont have a great OS like Windows for you to start your computer knowledge with. Well, this is just my point of view, but you can argue.
Tuesday, April 17, 2007
Tactical VoIP Toolkit Released
Guys, if you are into VoIP auditing, the Grugq has finally released his long waited Tactical VoIP Toolkit. I was using this tool at HiTB when he first released it to the students attending his training. It was written in Python and best of all, it is customizable. You can write your own VoIP security tools on top of the Toolkit. This makes it very portable and flexible in terms of the tool's function. Well, currently there is only siping and ravage but its sufficient enough to perform basic audit and analyzation.
"The Tactical VoIP Toolkit (TacVTK) is a collection of tools designed specifically for VoIP security assessment. The TacVTK's functionality will expand in as new tools are developed and integrated."
Please visit the Grugq's site at http://www.tacticalvoip.com to download this free and powerful tool. Hey Grugq, big ups to you. :)
"The Tactical VoIP Toolkit (TacVTK) is a collection of tools designed specifically for VoIP security assessment. The TacVTK's functionality will expand in as new tools are developed and integrated."
Please visit the Grugq's site at http://www.tacticalvoip.com to download this free and powerful tool. Hey Grugq, big ups to you. :)
Monday, April 16, 2007
Wapiti and proxmon
I was posting on Rsnake's forum about web penetration testing tools that most web application pentesters used. For me, i only use webscarab, XSS cheatsheet from Rsnake, wikto and firefox addons like tamper data and live http headers for my testings. These tools are good enough for me to get the job done most of the time. Sometimes, it depends how much i want to actually break into systems during a test. If the application has a lot of vulnerabilities during a simple scan, it is nuff said, please patch your system. Else if the application is robust enough, i am very determine to actually dig in further to uncover flaws.
The other night, jeremiah posted a topic on "Vulnerability Assessment, When do we stop looking? " and i commented that if the application is vulnerable to simple scans, then it is not worth to dig in further, else if the application is robust, it is worth every single effort to explore more flaws. And when do we stop? It all depends on how much you think the application has serious vulnerabilities. As i was commenting on his blog, i was thinking of a tool that can simplify my process of auditing and i happen to read on jungsonn comments. He recommended a very useful tool that i am going to test it once i finished my project over here. Yes its hectic here and sorry for the lack of updates guys. Here is a short excerpt.
Wapiti:
* File Handling Errors (Local and remote include/require, fopen, readfile…)
* Database Injection (PHP/JSP/ASP SQL Injections and XPath Injections)
* XSS (Cross Site Scripting) Injection
* LDAP Injection
* Command Execution detection (eval(), system(), passtru()…)
* CRLF Injection (HTTP Response Splitting, session fixation…)
I managed to test it a little and it seems to be a good tool to use and the best of all, its open source which means it is free!! You will need python to use this tool. More can be found here: http://wapiti.sourceforge.net
As i was playing around his tool, i was thinking about blackhat. I want to see what is the latest exploits that security researchers found and i stumble across another web application pentesting tool. Its proxmon. It was written by Jonathan Wilkins and he presented in Blackhat Europe 2007, so i guess it wouldn't be a bad tool to use. A sample of the tool output is shown as below:
[*] starting ProxMon v1.0.15 (http://www.isecpartners.com)
[*] Copyright (C) 2007, Jonathan Wilkins, iSEC Partners Inc.
[*] Proxmon comes with ABSOLUTELY NO WARRANTY;
[*] This is free software, and you are welcome to redistribute it
[*] under certain conditions; see accompanying file LICENSE for
[*] details on warranty and redistribution details.
[*] Loading support for: WebScarab
[*] Loading Checks ...
- Find interesting comments
- Find cookie values that also are sent on the query string
- Find HTTP Basic or Digest Authentication usage
- Identify frameworks and scripts in use by server
- Find dangerous functions in JavaScript code
- Find offsite redirects
- Find cookies with the secure flag that also get sent cleartext
- Find values set over SSL that later go cleartext
- Find values sent to other domains
- Find common undesirable directories
- Find files that indicate common vulnerabilities
- Find directories that allow directory listing
- Find SSL server configuration issues
- Find directories writable via PUT
[*] 14 checks loaded
[*] Finding available sessions ...
[*] Processing session test/webscarab in test
[*] Running in monitor mode
[*] Monitoring test/webscarab
[*] Parsing existing conversations ...
[*] Interesting comment: XXX in http://scratch.bitland.net:80/ (TIDs: 35)
[*] Interesting comment: bug in http://www.bitland.net:80/ (TIDs: 532)
[*] Interesting comment: TODO in http://scratch.bitland.net:80/ (TIDs: 35)
[*] Interesting comment: ??? in http://scratch.bitland.net:80/ (TIDs: 35)
[*] Interesting comment: !!! in http://scratch.bitland.net:80/ (TIDs: 35)
[*] Cookie value seen on QS: secret1 (Secure, SSL) (TIDs: 16)
[*] Cookie value seen on QS: secret2 (Secure, SSL) (TIDs: 9)
[*] Digest auth seen: Authorization: Digest username='jwilkins', realm='scratchdigest', [snip ...] (TIDs: 34)
[*] Basic auth seen: Authorization: Basic andpbGtpbnM6YXNkZmFzZGY= (TIDs: 31, 32)
[*] IDed framework: scratch.bitland.net:80 is using PHP/5.2.1 (http://www.php.net) (TIDs: 35)
[*] IDed framework: www.isecpartners.com:80 is using YUI/1.2.3 (http://developer.yahoo.com/yui) (TIDs: 16)
[*] Unsafe JavaScript found: eval at http://scratch.bitland.net:80/:15 (TIDs: 35)
[*] Unsafe JavaScript found: eval at http://scratch.bitland.net:80/:16 (TIDs: 35)
[*] Secure cookie value sent clear: secret2 (TIDs: 7, 9)
[*] Secure cookie value sent clear: secret1 (TIDs: 16, 36)
[*] Value set over SSL sent clear: secret2 as secure2 (TIDs: 7)
[*] Value set over SSL sent clear: secret2 as bar (TIDs: 9)
[*] Value set over SSL sent clear: secret1 as foobar (TIDs: 16)
[*] Value set over SSL sent clear: secret1 as asdf (TIDs: 36)
[*] Value (secret1) sent to multiple domains: bitland.net (TIDs: 5, 6, 36)
[*] Value (secret1) sent to multiple domains: isecpartners.com (TIDs: 16)
[*] Bad directory found: /backup/ on scratch.bitland.net:80 (TIDs: 0)
[*] Bad file found: /environ.pl on scratch.bitland.net:80 (TIDs: 0)
[*] Listing of /listable/ on scratch.bitland.net:80 succeeded (TIDs: 0)
[*] SSL Config issue https://www.bitland.net:443: aNULL null cipher (TIDs: 0)
[*] SSL Config issue https://www.bitland.net:443: Export strength ciphers (TIDs: 0)
[*] SSL Config issue https://www.bitland.net:443: 40 bit Export strength ciphers (TIDs: 0)
[*] SSL Config issue https://www.bitland.net:443: Low strength ciphers (TIDs: 0)
[*] SSL Config issue https://www.bitland.net:443: SSLv2 protocol (TIDs: 0)
[*] Upload to /put/ on scratch.bitland.net:80 succeeded (TIDs: 0)
[*] Parsed 38 existing conversations
[*] Session is not active, no point in monitoring
The other night, jeremiah posted a topic on "Vulnerability Assessment, When do we stop looking? " and i commented that if the application is vulnerable to simple scans, then it is not worth to dig in further, else if the application is robust, it is worth every single effort to explore more flaws. And when do we stop? It all depends on how much you think the application has serious vulnerabilities. As i was commenting on his blog, i was thinking of a tool that can simplify my process of auditing and i happen to read on jungsonn comments. He recommended a very useful tool that i am going to test it once i finished my project over here. Yes its hectic here and sorry for the lack of updates guys. Here is a short excerpt.
Wapiti:
* File Handling Errors (Local and remote include/require, fopen, readfile…)
* Database Injection (PHP/JSP/ASP SQL Injections and XPath Injections)
* XSS (Cross Site Scripting) Injection
* LDAP Injection
* Command Execution detection (eval(), system(), passtru()…)
* CRLF Injection (HTTP Response Splitting, session fixation…)
I managed to test it a little and it seems to be a good tool to use and the best of all, its open source which means it is free!! You will need python to use this tool. More can be found here: http://wapiti.sourceforge.net
As i was playing around his tool, i was thinking about blackhat. I want to see what is the latest exploits that security researchers found and i stumble across another web application pentesting tool. Its proxmon. It was written by Jonathan Wilkins and he presented in Blackhat Europe 2007, so i guess it wouldn't be a bad tool to use. A sample of the tool output is shown as below:
[*] starting ProxMon v1.0.15 (http://www.isecpartners.com)
[*] Copyright (C) 2007, Jonathan Wilkins, iSEC Partners Inc.
[*] Proxmon comes with ABSOLUTELY NO WARRANTY;
[*] This is free software, and you are welcome to redistribute it
[*] under certain conditions; see accompanying file LICENSE for
[*] details on warranty and redistribution details.
[*] Loading support for: WebScarab
[*] Loading Checks ...
- Find interesting comments
- Find cookie values that also are sent on the query string
- Find HTTP Basic or Digest Authentication usage
- Identify frameworks and scripts in use by server
- Find dangerous functions in JavaScript code
- Find offsite redirects
- Find cookies with the secure flag that also get sent cleartext
- Find values set over SSL that later go cleartext
- Find values sent to other domains
- Find common undesirable directories
- Find files that indicate common vulnerabilities
- Find directories that allow directory listing
- Find SSL server configuration issues
- Find directories writable via PUT
[*] 14 checks loaded
[*] Finding available sessions ...
[*] Processing session test/webscarab in test
[*] Running in monitor mode
[*] Monitoring test/webscarab
[*] Parsing existing conversations ...
[*] Interesting comment: XXX in http://scratch.bitland.net:80/ (TIDs: 35)
[*] Interesting comment: bug in http://www.bitland.net:80/ (TIDs: 532)
[*] Interesting comment: TODO in http://scratch.bitland.net:80/ (TIDs: 35)
[*] Interesting comment: ??? in http://scratch.bitland.net:80/ (TIDs: 35)
[*] Interesting comment: !!! in http://scratch.bitland.net:80/ (TIDs: 35)
[*] Cookie value seen on QS: secret1 (Secure, SSL) (TIDs: 16)
[*] Cookie value seen on QS: secret2 (Secure, SSL) (TIDs: 9)
[*] Digest auth seen: Authorization: Digest username='jwilkins', realm='scratchdigest', [snip ...] (TIDs: 34)
[*] Basic auth seen: Authorization: Basic andpbGtpbnM6YXNkZmFzZGY= (TIDs: 31, 32)
[*] IDed framework: scratch.bitland.net:80 is using PHP/5.2.1 (http://www.php.net) (TIDs: 35)
[*] IDed framework: www.isecpartners.com:80 is using YUI/1.2.3 (http://developer.yahoo.com/yui) (TIDs: 16)
[*] Unsafe JavaScript found: eval at http://scratch.bitland.net:80/:15 (TIDs: 35)
[*] Unsafe JavaScript found: eval at http://scratch.bitland.net:80/:16 (TIDs: 35)
[*] Secure cookie value sent clear: secret2 (TIDs: 7, 9)
[*] Secure cookie value sent clear: secret1 (TIDs: 16, 36)
[*] Value set over SSL sent clear: secret2 as secure2 (TIDs: 7)
[*] Value set over SSL sent clear: secret2 as bar (TIDs: 9)
[*] Value set over SSL sent clear: secret1 as foobar (TIDs: 16)
[*] Value set over SSL sent clear: secret1 as asdf (TIDs: 36)
[*] Value (secret1) sent to multiple domains: bitland.net (TIDs: 5, 6, 36)
[*] Value (secret1) sent to multiple domains: isecpartners.com (TIDs: 16)
[*] Bad directory found: /backup/ on scratch.bitland.net:80 (TIDs: 0)
[*] Bad file found: /environ.pl on scratch.bitland.net:80 (TIDs: 0)
[*] Listing of /listable/ on scratch.bitland.net:80 succeeded (TIDs: 0)
[*] SSL Config issue https://www.bitland.net:443: aNULL null cipher (TIDs: 0)
[*] SSL Config issue https://www.bitland.net:443: Export strength ciphers (TIDs: 0)
[*] SSL Config issue https://www.bitland.net:443: 40 bit Export strength ciphers (TIDs: 0)
[*] SSL Config issue https://www.bitland.net:443: Low strength ciphers (TIDs: 0)
[*] SSL Config issue https://www.bitland.net:443: SSLv2 protocol (TIDs: 0)
[*] Upload to /put/ on scratch.bitland.net:80 succeeded (TIDs: 0)
[*] Parsed 38 existing conversations
[*] Session is not active, no point in monitoring
Sunday, April 15, 2007
Cisco Catalyst 6000, 6500 Series and Cisco 7600 Series NAM Vulnerability
"Cisco Catalyst 6000, 6500 series and Cisco 7600 series that have a Network Analysis Module installed are vulnerable to an attack, which could allow an attacker to gain complete control of the system. Only Cisco Catalyst systems that have a NAM on them are affected. This vulnerability affects systems that run Internetwork Operating System(IOS) or Catalyst Operating System (CatOS)."
More information can be found here:
http://www.cisco.com/warp/public/707/cisco-sa-20070228-nam.shtml
"NAMs communicate with the Catalyst system by using the Simple Network Management Protocol (SNMP). By spoofing the SNMP communication between the Catalyst system and the NAM an attacker may obtain complete control of the Catalyst system."
More information can be found here:
http://www.cisco.com/warp/public/707/cisco-sa-20070228-nam.shtml
"NAMs communicate with the Catalyst system by using the Simple Network Management Protocol (SNMP). By spoofing the SNMP communication between the Catalyst system and the NAM an attacker may obtain complete control of the Catalyst system."
Friday, April 13, 2007
Cisco PIX PFM plaintext password revealed
For those who are using PIX Firewall Manager to configure and manage your firewall, you are at risk of your firewall password being obtained by an intruder or an insider. Why? Because after the PFM software makes an initial connection to the PIX Firewall, the administrative password is stored in plaintext on the local management workstation. I am not too where is it stored, but it might be in the registry or search for the PFM installation directory for log or text files. It might be inside. So, to avoid that, cisco recommends using PIX Device Manager(PDM) instead. Well, for me, i never use PDM or PFM to configure the firewall, the IOS itself is good enough for me. Also, always practice logging your PC after finished using. The default username and password for the PFM is as shown below:
Administrator username: pixadmin
Administrator password: cisco
Normal user username: pixuser
Normal user password: cisco
Change your default user accounts to avoid compromisation.
Administrator username: pixadmin
Administrator password: cisco
Normal user username: pixuser
Normal user password: cisco
Change your default user accounts to avoid compromisation.
Thursday, April 12, 2007
NACAttack BlackHat Europe 2007
Last night i blogged about the possible of NAC attack. Today, i found out that this had already been presented. Ok, i know i am slow catching up but both the german researchers managed to spoof the posture validation between a Cisco Trust Agent to the Cisco ACS (Access Control Server), and to gain access to the network even if the element is not compliant with the posture validation checks. To download the presentation and whitepapers, go to: http://www.blackhat.com/html/bh-media-archives/bh-archives-2007.html#eu
Wednesday, April 11, 2007
Hacking Cisco NAC - NACATTACK
Dror-John Roecher and Michael Thumann who were able to hack the Cisco NAC solution by exploiting a fundamental design flaw. In this video they illustrate how they worked towards this discovery and give us some exploit details. It is not their intention to simply release a tool, they want the audience to understand how Cisco NAC works and why it is not as secure as Cisco wants us to believe.
Tuesday, April 10, 2007
Defeating Evil Twin
The other day i was discussing with thrill about detecting and defeating Evil Twin and what are the best options beside using WEP or WPA. For folks who still don't know, both WEP and WPA can be broken and is not considered secure. Check my previous post and you will find the tools needed to break those keys. Apparently, it boils down to two options, but i will let you guys decide which one is more secure.
Thrill was suggesting about placing an Access Point in the DMZ area and make the IP a private one. A VPN server would also be needed to be setup in the DMZ area for listening to clients who wants to connect to the AP and use the wireless service. In that manner, an attacker who tries to setup an Evil Twin will not have access to the DMZ area because he would first need to use a VPN client to connect to the VPN server before any surfing can continue. This has several advantages and disadvantages and it all depends how you looked at it. The advantages being that all the traffic will be encrypted because it will be tunneled through a VPN server first before going out to the internet. Second being that SSID can be broadcast and no WEP/WPA security is needed. Of course if you are being paranoid, you can also include WPA key as an option. And third, it will defeat most Evil Twin. Below is a diagram which depicts the whole scenario.

According to thrill, its not necessary to implement a DMZ zone. It could be another extra network card on the VPN server that is going to have itself and the AP connected to it. Thrill quoted: "The trick is to not allow routing through this interface, and to set up a VPN server on that machine listening ONLY on that interface. And maybe a DHCP server on that interface as well. This is how this network becomes secure, and someone setting up an Evil Twin wouldn't be able to duplicate. And even if they did, the VPN client can be set up to authenticate a server side certificate easy enough." I wont say this is 100% secure, but it is the best solution he can think of and i do agree that it is good solution. The downside of this setup is every user needs to install OpenVPN client software on their machine and needs to be notified of the setup. That's a hassle.
On the other side, thrill also quote: "using 802.1x authentication along with using a Radius server for logging in the user. Some of you may have already heard of the technology, it's using the Odyssey client by Funk Software, along with their Steel Belted Radius. Using Cisco APs we were able to enable rotating WEP keys that were only given to the client if their Certificate could be authenticated, once they were connected to the wireless network, they then needed to authenticate their user/password via the radius which pointed to the LDAP portion of AD. The trick for rotating SSID/WEP keys is using a certificate to authenticate to the actual AP. The AP is set up to point to a radius server which has the certificate on it, then the client sends the AP the supplication requesting the SSID/Key, the AP forwards the request to the Radius server which authenticates the certificate and sends an OK to the AP, who in turn sends the client the SSID/Key to authenticate." Below depicts the scenarion:

Whichever is better, if something becomes too hard to use or requires too many steps, most people will be lazy and don't care about it. But then again, it all depends on the organization on how they want to implement their systems. Just my opinion.
Thrill was suggesting about placing an Access Point in the DMZ area and make the IP a private one. A VPN server would also be needed to be setup in the DMZ area for listening to clients who wants to connect to the AP and use the wireless service. In that manner, an attacker who tries to setup an Evil Twin will not have access to the DMZ area because he would first need to use a VPN client to connect to the VPN server before any surfing can continue. This has several advantages and disadvantages and it all depends how you looked at it. The advantages being that all the traffic will be encrypted because it will be tunneled through a VPN server first before going out to the internet. Second being that SSID can be broadcast and no WEP/WPA security is needed. Of course if you are being paranoid, you can also include WPA key as an option. And third, it will defeat most Evil Twin. Below is a diagram which depicts the whole scenario.

According to thrill, its not necessary to implement a DMZ zone. It could be another extra network card on the VPN server that is going to have itself and the AP connected to it. Thrill quoted: "The trick is to not allow routing through this interface, and to set up a VPN server on that machine listening ONLY on that interface. And maybe a DHCP server on that interface as well. This is how this network becomes secure, and someone setting up an Evil Twin wouldn't be able to duplicate. And even if they did, the VPN client can be set up to authenticate a server side certificate easy enough." I wont say this is 100% secure, but it is the best solution he can think of and i do agree that it is good solution. The downside of this setup is every user needs to install OpenVPN client software on their machine and needs to be notified of the setup. That's a hassle.
On the other side, thrill also quote: "using 802.1x authentication along with using a Radius server for logging in the user. Some of you may have already heard of the technology, it's using the Odyssey client by Funk Software, along with their Steel Belted Radius. Using Cisco APs we were able to enable rotating WEP keys that were only given to the client if their Certificate could be authenticated, once they were connected to the wireless network, they then needed to authenticate their user/password via the radius which pointed to the LDAP portion of AD. The trick for rotating SSID/WEP keys is using a certificate to authenticate to the actual AP. The AP is set up to point to a radius server which has the certificate on it, then the client sends the AP the supplication requesting the SSID/Key, the AP forwards the request to the Radius server which authenticates the certificate and sends an OK to the AP, who in turn sends the client the SSID/Key to authenticate." Below depicts the scenarion:

Whichever is better, if something becomes too hard to use or requires too many steps, most people will be lazy and don't care about it. But then again, it all depends on the organization on how they want to implement their systems. Just my opinion.
Monday, April 9, 2007
Rsnake and Jeremiah new XSS book
Becoming an Ethical hacker.
For those of you who wished to be a hacker, you will need some small little tricks here and there and of course, a great deal of knowledge will help. There is a pdf out on the internet which actually shows you how you can become a hacker. Some of you might have actually got it, but well, for those who wants to become a hacker and wants to know the jack of all trades in hacking, do a simple google dorking with:
filetype:pdf "Becoming a Hacker – Part 1"
Download the pdf and there you learn hacking. Let me know what you guys think?
Disclaimer: Please do not use this document that you downloaded to perform any illegal activities. I will not hold any responsibility on this matter.
filetype:pdf "Becoming a Hacker – Part 1"
Download the pdf and there you learn hacking. Let me know what you guys think?
Disclaimer: Please do not use this document that you downloaded to perform any illegal activities. I will not hold any responsibility on this matter.
Sunday, April 8, 2007
Verifying authencation mechanism used in routing protocls
Way back in my previous post, i had given a list of audting commands to follow when performing auditing of Cisco routers. Now its time to verify if the protocols themselves are using authentication mechanism to defeat most of the attacks. Most of the time after a penetration test, if you find telnet port open, you would suggest the client to use SSH instead of telnet. This is ok, because it is easy to migrate the protocols. What if SNMP port is open? Do you tell the client to disable it because it is vulnerable to attacks or would you suggest the client to upgrade to the lastest version? What about compatibility and interoperability issues between SNMPv2 and SNMPv3? What if the client needs this protocol for monitoring purposes? Well, I guess there is always solution to everything. I will show you steps where you can perform to ensure that the "vulnerable" protocol is at least safe from 70% of the attacks.
SNMP: Make sure access-list is used to limit machines that is allowed to access to router. For example, see the following commands:
Setting the access-list to permit only IPs that are allowed to access the router.
access−list 12 permit 192.168.1.1
access−list 13 permit 192.168.1.2
The command below sets the community string which is sort like a password to access-list 28 and 29. Of course, you should set a very strong community to avoid brute-force or dictionary attacks.
snmp−server community cisco1 RW 28
snmp−server community cisco2 RO 29
The command below allow the router to send traps to the SNMP Manager machine
snmp−server host 192.168.1.1 cisco1 snmp
snmp−server host 192.168.1.2 cisco2 snmp
So by using the access-list command, only the allowed hosts are able to perform the necessary tasks.
RIP: RIPv1 does not support any authentication, instead it is using plain text for routing purposes. However, RIPv2 support both plain text and md5 authentication. When auditing an IOS config file, check for the following key words:
key chain cisco
key 1
key−string rip
ip rip authentication key−chain cisco
ip rip authentication mode md5
To allow routing protocol authentication, the key chain command will identify a group of authentication keys, the key command will identify an authentication key on a key chain and the key-string command will specify the authentication string for a key. On top of it, make sure that the command ip rip authentication mode md5 is enabled for RIP updates.
EIGRP: The same goes for EIGRP. The commands to check for EIGRP is identical to RIP as shown below:
key chain cisco
key 1
key−string eigrp
ip authentication mode eigrp 10 md5
ip authentication key−chain eigrp 10 cisco
Please note that the command ip authentication mode eigrp 10 md5 is different from RIP's ip authentication mode md5. The "eigrp 10" is intepreted as eigrp, so please take note of that.
OSPF: OSPF supports both plain text and md5 authentication. You can choose either one of the authentication method depending on your preference. Some routers might not support the md5 authentication, so that leaves you with no choice but to use plain text authention. Else, deploy md5 authentication which is 100 times more secure. Check for these commands below to see if the router is using any authentication.
For plain text authentication:
ip ospf authentication−key cisco
area 0 authentication
For md5 authentication:
ip ospf message−digest−key 40 md5 cisco
area 0 authentication message−digest
Please note that the value of the key-id which is 40 allows passwords to be changed without having to disable authentication.
So above is a quick list to check for authentication on routing protocols. If you happen to have a chance to audit a router config file, just a glance will tell you how good is the network administrator is.
To know more about the commands usage and its meaning, refer to http://cco.cisco.com/en/US/products/sw/iosswrel/ps5187/products_command_reference_chapter09186a008017d029.html
SNMP: Make sure access-list is used to limit machines that is allowed to access to router. For example, see the following commands:
Setting the access-list to permit only IPs that are allowed to access the router.
access−list 12 permit 192.168.1.1
access−list 13 permit 192.168.1.2
The command below sets the community string which is sort like a password to access-list 28 and 29. Of course, you should set a very strong community to avoid brute-force or dictionary attacks.
snmp−server community cisco1 RW 28
snmp−server community cisco2 RO 29
The command below allow the router to send traps to the SNMP Manager machine
snmp−server host 192.168.1.1 cisco1 snmp
snmp−server host 192.168.1.2 cisco2 snmp
So by using the access-list command, only the allowed hosts are able to perform the necessary tasks.
RIP: RIPv1 does not support any authentication, instead it is using plain text for routing purposes. However, RIPv2 support both plain text and md5 authentication. When auditing an IOS config file, check for the following key words:
key chain cisco
key 1
key−string rip
ip rip authentication key−chain cisco
ip rip authentication mode md5
To allow routing protocol authentication, the key chain command will identify a group of authentication keys, the key command will identify an authentication key on a key chain and the key-string command will specify the authentication string for a key. On top of it, make sure that the command ip rip authentication mode md5 is enabled for RIP updates.
EIGRP: The same goes for EIGRP. The commands to check for EIGRP is identical to RIP as shown below:
key chain cisco
key 1
key−string eigrp
ip authentication mode eigrp 10 md5
ip authentication key−chain eigrp 10 cisco
Please note that the command ip authentication mode eigrp 10 md5 is different from RIP's ip authentication mode md5. The "eigrp 10" is intepreted as eigrp
OSPF: OSPF supports both plain text and md5 authentication. You can choose either one of the authentication method depending on your preference. Some routers might not support the md5 authentication, so that leaves you with no choice but to use plain text authention. Else, deploy md5 authentication which is 100 times more secure. Check for these commands below to see if the router is using any authentication.
For plain text authentication:
ip ospf authentication−key cisco
area 0 authentication
For md5 authentication:
ip ospf message−digest−key 40 md5 cisco
area 0 authentication message−digest
Please note that the value of the key-id which is 40 allows passwords to be changed without having to disable authentication.
So above is a quick list to check for authentication on routing protocols. If you happen to have a chance to audit a router config file, just a glance will tell you how good is the network administrator is.
To know more about the commands usage and its meaning, refer to http://cco.cisco.com/en/US/products/sw/iosswrel/ps5187/products_command_reference_chapter09186a008017d029.html
Saturday, April 7, 2007
Cisco IOS CLI regular expressions, Part II — ‘AND’
Handsomeplanet wrote about using regex in IOS which is a good idea to see it live.
Here’s a scenario: you’re auditing one of your routers, checking to make sure privilege levels are what they should be for individual users, and that commands that have been moved into non-default privilege levels that appear to be correctly defined.
Here’s the output of ’show running-config’ with only lines that match ‘privi’ included (so as to catch lines that show privilege levels:
IOS-rtr#sh run | inc privi
username sneezy privilege 0 secret 5 $1$Dz6cKoEINsYusITt.l
username dopey privilege 0 secret 5 $1$MIUYWJ.I3iGq/qNleB.
username meson privilege 0 secret 5 $1$7uBWyjan.5JB8KHR0
username gluon privilege 15 secret 5 $1$VuoC$09dsgXRB.A/d
privilege exec level 0 traceroute
privilege exec level 0 ping
privilege exec all level 0 show
privilege exec level 0 clear ip nat translation
privilege exec level 0 clear ip nat
privilege exec level 0 clear ip
privilege exec level 0 clear
privilege configure level 7 logging
privilege configure level 7 logging trap
privilege configure level 7 logging source
privilege level 15
privilege level 15
In this case, you can use the regular expression “.*” (dot-star) to match lines that contain both the word ‘privilege’ and ‘level 0′, thus eliminating other priv levels, as well as username definitions:
IOS-rtr#sh run | inc privi.*level 0
privilege exec level 0 traceroute
privilege exec level 0 ping
privilege exec all level 0 show
privilege exec level 0 clear ip nat translation
privilege exec level 0 clear ip nat
privilege exec level 0 clear ip
privilege exec level 0 clear
The same thing works for an audit of ‘level 7′ commands:
OS-rtr#sh run | inc privi.*level 7
privilege configure level 7 logging
privilege configure level 7 logging trap
privilege configure level 7 logging source
If you want to show lines that match privilege levels other than zero, you could use this:
IOS-rtr#sh run | inc priv.*[1-9]
You should note that the “.*” (dot-star) regular expression can be used as a synonym for AND, provided that you are aware that “.*” is not order agnostic.
In order to do a true AND, you’d need an expression like :
sh run | inc (privi.*level 0|level 0.*privi)
This will match lines containing both ‘privilege’ and ‘level 0′, no matter which of the words appears first. To illustrate this, I’ll create a loopback interface (loop3) with some description text that will match the regex:
IOS-rtr#conf t
Enter configuration commands, one per line. End with CNTL/Z.
IOS-rtr(config)#int loop3
IOS-rtr(config-if)#desc level 0 is not privileged here!
IOS-rtr(config-if)#^Z
IOS-rtr#sh run | inc (privi.*level 0|level 0.*privi)
description level 0 is not privileged here!
privilege exec level 0 traceroute
privilege exec level 0 ping
privilege exec all level 0 show
privilege exec level 0 clear ip nat translation
privilege exec level 0 clear ip nat
privilege exec level 0 clear ip
privilege exec level 0 clear
It works! Notice that we caught both the description line and the privilege exec lines.
I guess I’m easily excited, but there it is. Next time I write about regular expressions for IOS, I’ll cover a kooky but somewhat useful use of ‘exclude’ that will get you just what you need from a list of dynamic switch MAC addresses.
Here’s a scenario: you’re auditing one of your routers, checking to make sure privilege levels are what they should be for individual users, and that commands that have been moved into non-default privilege levels that appear to be correctly defined.
Here’s the output of ’show running-config’ with only lines that match ‘privi’ included (so as to catch lines that show privilege levels:
IOS-rtr#sh run | inc privi
username sneezy privilege 0 secret 5 $1$Dz6cKoEINsYusITt.l
username dopey privilege 0 secret 5 $1$MIUYWJ.I3iGq/qNleB.
username meson privilege 0 secret 5 $1$7uBWyjan.5JB8KHR0
username gluon privilege 15 secret 5 $1$VuoC$09dsgXRB.A/d
privilege exec level 0 traceroute
privilege exec level 0 ping
privilege exec all level 0 show
privilege exec level 0 clear ip nat translation
privilege exec level 0 clear ip nat
privilege exec level 0 clear ip
privilege exec level 0 clear
privilege configure level 7 logging
privilege configure level 7 logging trap
privilege configure level 7 logging source
privilege level 15
privilege level 15
In this case, you can use the regular expression “.*” (dot-star) to match lines that contain both the word ‘privilege’ and ‘level 0′, thus eliminating other priv levels, as well as username definitions:
IOS-rtr#sh run | inc privi.*level 0
privilege exec level 0 traceroute
privilege exec level 0 ping
privilege exec all level 0 show
privilege exec level 0 clear ip nat translation
privilege exec level 0 clear ip nat
privilege exec level 0 clear ip
privilege exec level 0 clear
The same thing works for an audit of ‘level 7′ commands:
OS-rtr#sh run | inc privi.*level 7
privilege configure level 7 logging
privilege configure level 7 logging trap
privilege configure level 7 logging source
If you want to show lines that match privilege levels other than zero, you could use this:
IOS-rtr#sh run | inc priv.*[1-9]
You should note that the “.*” (dot-star) regular expression can be used as a synonym for AND, provided that you are aware that “.*” is not order agnostic.
In order to do a true AND, you’d need an expression like :
sh run | inc (privi.*level 0|level 0.*privi)
This will match lines containing both ‘privilege’ and ‘level 0′, no matter which of the words appears first. To illustrate this, I’ll create a loopback interface (loop3) with some description text that will match the regex:
IOS-rtr#conf t
Enter configuration commands, one per line. End with CNTL/Z.
IOS-rtr(config)#int loop3
IOS-rtr(config-if)#desc level 0 is not privileged here!
IOS-rtr(config-if)#^Z
IOS-rtr#sh run | inc (privi.*level 0|level 0.*privi)
description level 0 is not privileged here!
privilege exec level 0 traceroute
privilege exec level 0 ping
privilege exec all level 0 show
privilege exec level 0 clear ip nat translation
privilege exec level 0 clear ip nat
privilege exec level 0 clear ip
privilege exec level 0 clear
It works! Notice that we caught both the description line and the privilege exec lines.
I guess I’m easily excited, but there it is. Next time I write about regular expressions for IOS, I’ll cover a kooky but somewhat useful use of ‘exclude’ that will get you just what you need from a list of dynamic switch MAC addresses.
Frame-Relay explained
The other night i showed some frame-relay sample configuration and today i am going to blog more about frame-relay networks. Frame-relay is a reliable and inexpensive WAN protocol whereby it provides QoS service using DE bit, FECN and BECN bit. It also save cost for company who used to deploy leased-lines in the past by creating Permanent Virtual Circuit(PVC) with physical access lines. Before going further, below are some terms used the in Frame-relay terminology. I will not write a full article on frame-relay because the whole concept is so huge. I will just briefly describe how it works and its usage.
CIR Committed Information Rate [Guaranteed rate at which the network commits to transfer user data under normal conditions]
EIR Excess Information Rate [Maximum rate capactiy on top of CIR]
DLCI Data Link Connection Identifier [PVC end point connection identifier with only local significance]
LMI Local Management Interface [Maintenance protocol for frame-relay]
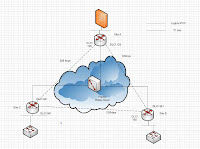
How frame-relay works is when the router forwards data to the frame-relay switch, the switch in turn forward the frames to the correct destination over a permanent virtual circuit. At each end of the PVC is identified with a DLCI value with only local significance value. A DLCI value is a 10-bit address in the frame-relay header which provides point-to-point or point-to-multipoint connection. I had drawn a simple diagram which depicts the explaination. For site A to send site B packets, it simply specifies the appropriate DLCI number for the virtual circuit that connects to Site B site in the Frame Relay header. However, please note that the DLCI value does not identify the whole PVC network, instead it is just the connection from your router to the frame-relay switch and when it reaches its destination, the DLCI might be a different value. That explains why it has only local significance. The CIR is the traffic rate at which it is guaranteed by your ISP. If packets are sent faster than the cIR rate which you had agreed with your ISP, your ISP might drop all or some of the excess packets depending on how the network is setup. A DE bit is set in the frame-relay header to indicate excess flow of the packets. So if the network is not congested, the packets will flow through, else the excess packets will be discarded. FECN and BECN are flags set in the frame-relay header to allow control of the congested traffic. If congestion is encountered during the traffic flow, the FECN flag will be set on the switch to indicate that there will be a delay of packets arrival and vice versa with the BECN flag set on the receiving frame-relay switch. In this manner, both the sending and the receiving router can expect congestion in the carrier network and delay of packets upon arrival. The LMI protocol is used for keepalive purposes and global addressing purpose like making the DLCI value to have a global significance. As you can see, i am just explaining in a very very basic manner, because the whole technology is so huge that you can even publish a entire book for it. Configuration wise, i had already shown you guys a few examples with basic and simple frame-relay setups. You guys can read more if you are interested. Just search in wiki or cisco.com and a wealth of information is waiting for you to explore. However, i am still exploring more options in terms of the configuration area.
How about spoofing frame-relay frames and reroute the whole traffic to a bogus network? Personally i had not tried it before because of cost and lack of resources. Secondly, i guess i do not touch frame-relay networks often. Well, if you guys knows how to do frame-relay rerouting or spoofing, let me know.
CIR Committed Information Rate [Guaranteed rate at which the network commits to transfer user data under normal conditions]
EIR Excess Information Rate [Maximum rate capactiy on top of CIR]
DLCI Data Link Connection Identifier [PVC end point connection identifier with only local significance]
LMI Local Management Interface [Maintenance protocol for frame-relay]
How frame-relay works is when the router forwards data to the frame-relay switch, the switch in turn forward the frames to the correct destination over a permanent virtual circuit. At each end of the PVC is identified with a DLCI value with only local significance value. A DLCI value is a 10-bit address in the frame-relay header which provides point-to-point or point-to-multipoint connection. I had drawn a simple diagram which depicts the explaination. For site A to send site B packets, it simply specifies the appropriate DLCI number for the virtual circuit that connects to Site B site in the Frame Relay header. However, please note that the DLCI value does not identify the whole PVC network, instead it is just the connection from your router to the frame-relay switch and when it reaches its destination, the DLCI might be a different value. That explains why it has only local significance. The CIR is the traffic rate at which it is guaranteed by your ISP. If packets are sent faster than the cIR rate which you had agreed with your ISP, your ISP might drop all or some of the excess packets depending on how the network is setup. A DE bit is set in the frame-relay header to indicate excess flow of the packets. So if the network is not congested, the packets will flow through, else the excess packets will be discarded. FECN and BECN are flags set in the frame-relay header to allow control of the congested traffic. If congestion is encountered during the traffic flow, the FECN flag will be set on the switch to indicate that there will be a delay of packets arrival and vice versa with the BECN flag set on the receiving frame-relay switch. In this manner, both the sending and the receiving router can expect congestion in the carrier network and delay of packets upon arrival. The LMI protocol is used for keepalive purposes and global addressing purpose like making the DLCI value to have a global significance. As you can see, i am just explaining in a very very basic manner, because the whole technology is so huge that you can even publish a entire book for it. Configuration wise, i had already shown you guys a few examples with basic and simple frame-relay setups. You guys can read more if you are interested. Just search in wiki or cisco.com and a wealth of information is waiting for you to explore. However, i am still exploring more options in terms of the configuration area.
How about spoofing frame-relay frames and reroute the whole traffic to a bogus network? Personally i had not tried it before because of cost and lack of resources. Secondly, i guess i do not touch frame-relay networks often. Well, if you guys knows how to do frame-relay rerouting or spoofing, let me know.

Dns-Pinning, the next big thing?
I always admire programmers for their sharp programming skills and their structured way of logical thinking. Me, myself can never be good in programming or scripting. I tried my times to brush up my skills, but always failed at some point. This is the reason why i choose networking over being a developer. If i am good in programming, i would definitely develop hell lot of security tools to cater the community. Now, this lead to a very interesting article i am going to refer you guys to. Have you guys heard of DNS-Pinning? I think its the "Next Big Thing" that is going to have effect on the web community after XSS and CSRF. Well, it all comes down to having ideas and working on a Proof of Concept. We all know that it is possible to port-scan using javascript with XSS and now comes DNS-Pinning. DNS-Pinning is like punching a hole in the firewall and allows scanning on a internal LAN. This is scary because it actually bypass the firewall rules and return all the open ports. I had just tested it on my machine and damn, the results are pretty accurate though. Read on for more information.
http://shampoo.antville.org/stories/1451301/
http://sla.ckers.org/forum/read.php?6,4511,9587#msg-9587
http://shampoo.antville.org/stories/1451301/
http://sla.ckers.org/forum/read.php?6,4511,9587#msg-9587
Friday, April 6, 2007
HiTB Aftermath
Guys, sorry for the lack of updates, i had been really with the HiTB conference. Anyway, last night was the last day of the HiTB conference and alas, i managed to get some well rested sleep. The event was crazy with lotsa security gurus chilling around. Well, i did not manage to capture a lot of images, but well i managed to get the Grugq and Dino to take a picture with me. As for the conference itself, i got to to say i was immensely captivated by the topic of "Robbing Banks: Easier Done Than Said" by Fabrice Marie. During the speech, he teaches you how ATM actually works and how easy it is to rob the bank unnoticingly. Well, you guys can do a google search and look for his past articles, its absolute awesome. Also, the Grugq gave us his insight view of how SIP is so unsecure and how easy it is to penetrate into networks using VoIP. Google him too and you will articles about him. As for me, i will get back on track soon as i have a lot of to catch up. Lastly but not least, i would have to recommend you guy to visit geek00l's blog. It is open source network security at its best. This guy is hell smart, as he dissect TCP and UDP packets like no others. Read to find out: http://geek00l.blogspot.com/

Fabrice in action

Mikko H. Hyppönen from F-Secure in action

Grugq and dino

A shot with Dino

A shot with The Grugq

I got a certificate of participation from Grugq

Fabrice in action

Mikko H. Hyppönen from F-Secure in action

Grugq and dino

A shot with Dino

A shot with The Grugq

I got a certificate of participation from Grugq
Wednesday, April 4, 2007
HiTB Live
Tuesday, April 3, 2007
Frame Relay configurations
I am still attending the VoIP hacking course by the Grugq. Its awesome and its better than anything on the market you had ever learned. Well, because of the hectic training, i don't have the time to blog much. Nevertheless, i still manage to make a snippet of my frame-relay configurations. And yes, once the conference is over, i am going to explore more about frame-relay. The examples below are just basics. Enjoy.

Configuring frame-relay broadcast

Configuring frame-relay point-to-point

Frame-relay configurations on a second router

Frame-relay point-to-point on the second router.

Configuring frame-relay broadcast

Configuring frame-relay point-to-point

Frame-relay configurations on a second router

Frame-relay point-to-point on the second router.
Monday, April 2, 2007
Cisco Next Generation Networks pt 1
Cisco NGN DDoS Strategy
Most of you should know what DDoS is what it can be a pain in the ass especially when all of your resources are being held up. DDoS are among the toughest to defend because of the large amount of bad traffic hogging up the network resources. Well, as always, Cisco is one company that is constantly seeking improvement on their products and they came up with Cisco Traffic Anomaly Detector and Cisco Guard.
How it works is that the Traffic Anomaly Detector actually does it job by creating a network traffic baseline of a zone. A zone can be a a farm of servers or IP addresses belonging to a network or subnet. This can be done by using a SPAN port on a switch to collect all the traffic and present it to the Anomaly Detector. Following that, you would have to perform threshold tuning and apply certain policies to protect the zone from being DDos. This can be done with the CLI or the web interface. I always prefer to use the CLI because of their rich and powerful features set. But as for visual effects like a graph to see if the traffic exceeds the threshold, a web interface can be deployed. I've got to say that this time round, Cisco has picked up on their security as they deployed SSH and SSL for remote connections. For using the web interface, a new command call service wbm needs to be enabled on the device along with an ACL like permit wbm 192.168.1.1 255.255.255.0 and permit ssh 192.168.1.1 255.255.255.0 to limit the configuration of the device only to certain IP addresses. Of course there are more commands like setting the filters, GUARD_zone, DETECTOR_zone and some others and i am only mentioning the basics.
So what happens when your network is under attack? The Anomaly Detector is smart enough to pass this "bad" traffic to the Cisco Guard and what this Guard does is it actually removes the "bad" traffic and reinject "good" traffic back to the attack zone, so that the zone can continue to function normally. The Guard itself has anti-DDoS mechanism build in it to prevent itself from being a DDoS target. As with the anomaly detector, settings need to be configured for the Guard. These will include zone creation, guard zone filters, zone traffic diversion and activating the zone protection. Most of these configurations must be done in CLI and as with the anomaly detector, it comes with web interface.
Personally, I don't think it is difficult to configure the Guard or the Anomaly Detector. It would be fun if i am given such an opportunity. Well, the above are just simple explaination of how the Next Generation Network DDoS stragety is going to be. Of course, you can still employ the old fashion of using a DDoS signature or IDS, but we are entering a whole new millenium of exciting features from Cisco and why not? Ya, i know you guys will say about the cost, but its always good to know new security features from Cisco. :)
Most of you should know what DDoS is what it can be a pain in the ass especially when all of your resources are being held up. DDoS are among the toughest to defend because of the large amount of bad traffic hogging up the network resources. Well, as always, Cisco is one company that is constantly seeking improvement on their products and they came up with Cisco Traffic Anomaly Detector and Cisco Guard.
How it works is that the Traffic Anomaly Detector actually does it job by creating a network traffic baseline of a zone. A zone can be a a farm of servers or IP addresses belonging to a network or subnet. This can be done by using a SPAN port on a switch to collect all the traffic and present it to the Anomaly Detector. Following that, you would have to perform threshold tuning and apply certain policies to protect the zone from being DDos. This can be done with the CLI or the web interface. I always prefer to use the CLI because of their rich and powerful features set. But as for visual effects like a graph to see if the traffic exceeds the threshold, a web interface can be deployed. I've got to say that this time round, Cisco has picked up on their security as they deployed SSH and SSL for remote connections. For using the web interface, a new command call service wbm needs to be enabled on the device along with an ACL like permit wbm 192.168.1.1 255.255.255.0 and permit ssh 192.168.1.1 255.255.255.0 to limit the configuration of the device only to certain IP addresses. Of course there are more commands like setting the filters, GUARD_zone, DETECTOR_zone and some others and i am only mentioning the basics.
So what happens when your network is under attack? The Anomaly Detector is smart enough to pass this "bad" traffic to the Cisco Guard and what this Guard does is it actually removes the "bad" traffic and reinject "good" traffic back to the attack zone, so that the zone can continue to function normally. The Guard itself has anti-DDoS mechanism build in it to prevent itself from being a DDoS target. As with the anomaly detector, settings need to be configured for the Guard. These will include zone creation, guard zone filters, zone traffic diversion and activating the zone protection. Most of these configurations must be done in CLI and as with the anomaly detector, it comes with web interface.
Personally, I don't think it is difficult to configure the Guard or the Anomaly Detector. It would be fun if i am given such an opportunity. Well, the above are just simple explaination of how the Next Generation Network DDoS stragety is going to be. Of course, you can still employ the old fashion of using a DDoS signature or IDS, but we are entering a whole new millenium of exciting features from Cisco and why not? Ya, i know you guys will say about the cost, but its always good to know new security features from Cisco. :)
Sunday, April 1, 2007
Subscribe to:
Posts (Atom)












