Ok, its easy to detect cisco routers and there is no doubt about it. Traceroute is a utility to discover the routers and firewalls and i shan't go deep into it. If telnet is opened after performing a port scan, just telnet to the IP address and look at the banner and it will say something like
User access verification. And there you go, you just discovered a cisco router or core switch on the internet. Well, thats easy.
Port Scanners are one of the best tool to discover open ports. A vulnerable cisco router with default settings will have many ports open. It just take one vulnerable open port to actually bring the router down. Well, i shan't go too deep on that too. The best port scanners out there that would perform the job would be nmap, unicornscan, hping, sinfp, p0f, xprobe and many others. Do not use these tools without permission to scan the networks. Well, i had been performing pentest for the past 4 years and today i managed to captured screenshots of port scanning my servers.
If you ever find a cisco product and had permission to scan, you can try to use the switches as seen on the screenshots.

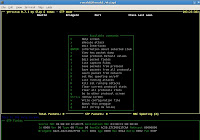
Above shows nmap scans on a server. Observe the switches. Of course there are many more switches. These are the ones i normally use.

Above shows the hping scans, notice that the S..A bit is returned back. If you know the TCP/IP three way handshake, this indicates that the ports are opened. Personally, i like using hping, it is a powerful low level TCP/IP tool.


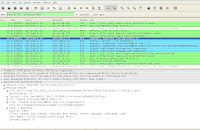
Above diagram shows the Unicornscan, another powerful scanner. This scanner can be used to scan for large networks and can be used to perform DoS. In addition, it is also very very fast. I had attached the results below. There is also tools like sinfp, p0f and xprobe, i shant mention too much here, you can search for it.
BT ~ # unicornscan -mT -vvv -I -r300 -E 192.168.1.55
adding 192.168.1.55/32 mode `TCPscan' ports `7,9,11,13,18,19,21-23,25,37,39,42,49,50,53,65,67-70,79-81,88,98,100,105-107,109-111,113,118,119,123,129,135,137-139,143,150,161-164,174,177-179,191,199-202,204,206,209,210,213,220,345,346,347,369-372,389,406,407,422,443-445,487,500,512-514,517,518,520,525,533,538,548,554,563,587,610-612,631-634,636,642,653,655,657,666,706,750-752,765,779,808,873,901,923,941,946,992-995,1001,1023-1030,1080,1210,1214,1234,1241,1334,1349,1352,1423-1425,1433,1434,1524,1525,1645,1646,1649,1701,1718,1719,1720,1723,1755,1812,1813,2048-2050,2101-2104,2140,2150,2233,2323,2345,2401,2430,2431,2432,2433,2583,2628,2776,2777,2988,2989,3050,3130,3150,3232,3306,3389,3456,3493,3542-3545,3632,3690,3801,4000,4400,4321,4567,4899,5002,5136-5139,5150,5151,5222,5269,5308,5354,5355,5422-5425,5432,5503,5555,5556,5678,6000-6007,6346,6347,6543,6544,6789,6838,6666-6670,7000-7009,7028,7100,7983,8079-8082,8088,8787,8879,9090,9101-9103,9325,9359,10000,10026,10027,10067,10080,10081,10167,10498,11201,15345,17001-17003,18753,20011,20012,21554,22273,26274,27374,27444,27573,31335-31338,31787,31789,31790,31791,32668,32767-32780,33390,47262,49301,54320,54321,57341,58008,58009,58666,59211,60000,60006,61000,61348,61466,61603,63485,63808,63809,64429,65000,65506,65530-65535' pps 300
using interface(s) eth0
added module payload for port 80 proto 6
added module payload for port 80 proto 6
added module payload for port 518 proto 17
added module payload for port 53 proto 17
added module payload for port 5060 proto 17
added module payload for port 1900 proto 17
scaning 1.00e+00 total hosts with 3.38e+02 total packets, should take a little longer than 8 Seconds
drone type Unknown on fd 3 is version 1.1
added module payload for port 80 proto 6
added module payload for port 80 proto 6
added module payload for port 518 proto 17
added module payload for port 53 proto 17
added module payload for port 5060 proto 17
added module payload for port 1900 proto 17
opening config file `/usr/local/etc/unicornscan/payloads.conf'
opening config file `/usr/local/etc/unicornscan/modules.conf'
drone type Unknown on fd 5 is version 1.1
scan iteration 1 out of 1
using pcap filter: `dst 192.168.58.129 and ! src 192.168.58.129 and (tcp or icmp)'
using TSC delay
TCP open 192.168.1.55:21 ttl 128
sender statistics 217.4 pps with 338 packets sent total
TCP--R----- 192.168.1.55:32769 ttl 128
TCP--R----- 192.168.1.55:1024 ttl 128
TCP--R----- 192.168.1.55:873 ttl 128
TCP--R----- 192.168.1.55:7001 ttl 128
TCP--R----- 192.168.1.55:1525 ttl 128
TCP--R----- 192.168.1.55:5423 ttl 128
TCP--R----- 192.168.1.55:1028 ttl 128
TCP--R----- 192.168.1.55:63809 ttl 128
TCP--R----- 192.168.1.55:2628 ttl 128
TCP--R----- 192.168.1.55:61603 ttl 128
TCP--R----- 192.168.1.55:53 ttl 128
TCP--R----- 192.168.1.55:54321 ttl 128
TCP--R----- 192.168.1.55:32771 ttl 128
TCP--R----- 192.168.1.55:2345 ttl 128
TCP--R----- 192.168.1.55:164 ttl 128
TCP--R----- 192.168.1.55:3306 ttl 128
TCP--R----- 192.168.1.55:22273 ttl 128
TCP--R----- 192.168.1.55:32768 ttl 128
TCP--R----- 192.168.1.55:1210 ttl 128
TCP--R----- 192.168.1.55:138 ttl 128
TCP--R----- 192.168.1.55:4899 ttl 128
TCP--R----- 192.168.1.55:204 ttl 128
TCP--R----- 192.168.1.55:32773 ttl 128
TCP--R----- 192.168.1.55:406 ttl 128
TCP--R----- 192.168.1.55:444 ttl 128
TCP--R----- 192.168.1.55:109 ttl 128
TCP--R----- 192.168.1.55:6347 ttl 128
TCP--R----- 192.168.1.55:150 ttl 128
TCP--R----- 192.168.1.55:5555 ttl 128
TCP--R----- 192.168.1.55:513 ttl 128
TCP--R----- 192.168.1.55:923 ttl 128
TCP--R----- 192.168.1.55:5002 ttl 128
TCP--R----- 192.168.1.55:8088 ttl 128
TCP--R----- 192.168.1.55:371 ttl 128
TCP--R----- 192.168.1.55:162 ttl 128
TCP--R----- 192.168.1.55:6007 ttl 128
TCP open 192.168.1.55:8081 ttl 128
TCP--R----- 192.168.1.55:6789 ttl 128
TCP--R----- 192.168.1.55:7983 ttl 128
TCP--R----- 192.168.1.55:5556 ttl 128
TCP--R----- 192.168.1.55:6668 ttl 128
TCP--R----- 192.168.1.55:177 ttl 128
TCP--R----- 192.168.1.55:512 ttl 128
TCP--R----- 192.168.1.55:2401 ttl 128
TCP--R----- 192.168.1.55:7007 ttl 128
TCP--R----- 192.168.1.55:1434 ttl 128
TCP--R----- 192.168.1.55:10067 ttl 128
TCP--R----- 192.168.1.55:32776 ttl 128
TCP--R----- 192.168.1.55:17003 ttl 128
TCP--R----- 192.168.1.55:518 ttl 128
TCP--R----- 192.168.1.55:10080 ttl 128
TCP--R----- 192.168.1.55:2776 ttl 128
TCP--R----- 192.168.1.55:65506 ttl 128
TCP--R----- 192.168.1.55:1701 ttl 128
TCP--R----- 192.168.1.55:10027 ttl 128
TCP open 192.168.1.55:139 ttl 128
TCP--R----- 192.168.1.55:1349 ttl 128
TCP--R----- 192.168.1.55:751 ttl 128
TCP--R----- 192.168.1.55:407 ttl 128
TCP--R----- 192.168.1.55:1025 ttl 128
TCP--R----- 192.168.1.55:61000 ttl 128
TCP--R----- 192.168.1.55:17002 ttl 128
TCP--R----- 192.168.1.55:6001 ttl 128
TCP--R----- 192.168.1.55:6000 ttl 128
TCP--R----- 192.168.1.55:191 ttl 128
TCP--R----- 192.168.1.55:992 ttl 128
TCP--R----- 192.168.1.55:213 ttl 128
TCP open 192.168.1.55:1027 ttl 128
TCP--R----- 192.168.1.55:58008 ttl 128
TCP--R----- 192.168.1.55:525 ttl 128
TCP--R----- 192.168.1.55:32770 ttl 128
TCP--R----- 192.168.1.55:64429 ttl 128
TCP--R----- 192.168.1.55:31789 ttl 128
TCP--R----- 192.168.1.55:209 ttl 128
TCP--R----- 192.168.1.55:5422 ttl 128
TCP--R----- 192.168.1.55:1755 ttl 128
TCP--R----- 192.168.1.55:6005 ttl 128
TCP--R----- 192.168.1.55:765 ttl 128
TCP--R----- 192.168.1.55:9101 ttl 128
TCP--R----- 192.168.1.55:32767 ttl 128
TCP--R----- 192.168.1.55:2050 ttl 128
TCP--R----- 192.168.1.55:3150 ttl 128
TCP--R----- 192.168.1.55:65534 ttl 128
TCP--R----- 192.168.1.55:1646 ttl 128
TCP--R----- 192.168.1.55:2103 ttl 128
TCP--R----- 192.168.1.55:47262 ttl 128
TCP--R----- 192.168.1.55:25 ttl 128
TCP--R----- 192.168.1.55:345 ttl 128
TCP--R----- 192.168.1.55:5137 ttl 128
TCP--R----- 192.168.1.55:113 ttl 128
TCP--R----- 192.168.1.55:7002 ttl 128
TCP--R----- 192.168.1.55:65533 ttl 128
TCP--R----- 192.168.1.55:5136 ttl 128
TCP--R----- 192.168.1.55:19 ttl 128
TCP--R----- 192.168.1.55:58666 ttl 128
TCP--R----- 192.168.1.55:5425 ttl 128
TCP--R----- 192.168.1.55:31336 ttl 128
TCP--R----- 192.168.1.55:9103 ttl 128
TCP--R----- 192.168.1.55:422 ttl 128
TCP--R----- 192.168.1.55:60000 ttl 128
TCP--R----- 192.168.1.55:10167 ttl 128
TCP--R----- 192.168.1.55:2140 ttl 128
TCP--R----- 192.168.1.55:657 ttl 128
TCP--R----- 192.168.1.55:161 ttl 128
TCP--R----- 192.168.1.55:129 ttl 128
TCP--R----- 192.168.1.55:9359 ttl 128
TCP--R----- 192.168.1.55:2048 ttl 128
TCP--R----- 192.168.1.55:636 ttl 128
TCP--R----- 192.168.1.55:1718 ttl 128
TCP--R----- 192.168.1.55:63485 ttl 128
TCP--R----- 192.168.1.55:1026 ttl 128
TCP--R----- 192.168.1.55:80 ttl 128
TCP--R----- 192.168.1.55:2432 ttl 128
TCP--R----- 192.168.1.55:79 ttl 128
TCP--R----- 192.168.1.55:6669 ttl 128
TCP--R----- 192.168.1.55:23 ttl 128
TCP--R----- 192.168.1.55:1645 ttl 128
TCP--R----- 192.168.1.55:118 ttl 128
TCP--R----- 192.168.1.55:210 ttl 128
TCP--R----- 192.168.1.55:5308 ttl 128
TCP--R----- 192.168.1.55:49301 ttl 128
TCP--R----- 192.168.1.55:7000 ttl 128
TCP--R----- 192.168.1.55:107 ttl 128
TCP--R----- 192.168.1.55:642 ttl 128
TCP--R----- 192.168.1.55:347 ttl 128
TCP--R----- 192.168.1.55:111 ttl 128
TCP--R----- 192.168.1.55:548 ttl 128
TCP--R----- 192.168.1.55:8787 ttl 128
TCP--R----- 192.168.1.55:3801 ttl 128
TCP--R----- 192.168.1.55:6667 ttl 128
TCP--R----- 192.168.1.55:6346 ttl 128
TCP--R----- 192.168.1.55:372 ttl 128
TCP--R----- 192.168.1.55:5222 ttl 128
TCP--R----- 192.168.1.55:9325 ttl 128
TCP--R----- 192.168.1.55:1812 ttl 128
TCP--R----- 192.168.1.55:5138 ttl 128
TCP--R----- 192.168.1.55:6670 ttl 128
TCP--R----- 192.168.1.55:31791 ttl 128
TCP--R----- 192.168.1.55:3130 ttl 128
TCP--R----- 192.168.1.55:9102 ttl 128
TCP--R----- 192.168.1.55:49 ttl 128
TCP--R----- 192.168.1.55:1524 ttl 128
TCP--R----- 192.168.1.55:31790 ttl 128
TCP--R----- 192.168.1.55:13 ttl 128
TCP--R----- 192.168.1.55:3389 ttl 128
TCP--R----- 192.168.1.55:666 ttl 128
TCP--R----- 192.168.1.55:98 ttl 128
TCP--R----- 192.168.1.55:3543 ttl 128
TCP--R----- 192.168.1.55:10081 ttl 128
TCP--R----- 192.168.1.55:70 ttl 128
TCP--R----- 192.168.1.55:6543 ttl 128
TCP--R----- 192.168.1.55:65000 ttl 128
TCP--R----- 192.168.1.55:1720 ttl 128
TCP--R----- 192.168.1.55:5139 ttl 128
TCP--R----- 192.168.1.55:68 ttl 128
TCP--R----- 192.168.1.55:6544 ttl 128
TCP--R----- 192.168.1.55:7005 ttl 128
TCP--R----- 192.168.1.55:22 ttl 128
TCP--R----- 192.168.1.55:9 ttl 128
TCP--R----- 192.168.1.55:1080 ttl 128
TCP--R----- 192.168.1.55:533 ttl 128
TCP--R----- 192.168.1.55:2430 ttl 128
TCP--R----- 192.168.1.55:123 ttl 128
TCP--R----- 192.168.1.55:370 ttl 128
TCP--R----- 192.168.1.55:1234 ttl 128
TCP--R----- 192.168.1.55:60006 ttl 128
TCP--R----- 192.168.1.55:520 ttl 128
TCP--R----- 192.168.1.55:32774 ttl 128
TCP--R----- 192.168.1.55:32668 ttl 128
TCP--R----- 192.168.1.55:2233 ttl 128
TCP--R----- 192.168.1.55:6006 ttl 128
TCP--R----- 192.168.1.55:612 ttl 128
TCP--R----- 192.168.1.55:65532 ttl 128
TCP--R----- 192.168.1.55:26274 ttl 128
TCP--R----- 192.168.1.55:88 ttl 128
TCP--R----- 192.168.1.55:995 ttl 128
TCP--R----- 192.168.1.55:50 ttl 128
TCP--R----- 192.168.1.55:538 ttl 128
TCP--R----- 192.168.1.55:2583 ttl 128
TCP--R----- 192.168.1.55:199 ttl 128
TCP--R----- 192.168.1.55:487 ttl 128
TCP--R----- 192.168.1.55:8879 ttl 128
TCP--R----- 192.168.1.55:2101 ttl 128
TCP--R----- 192.168.1.55:9090 ttl 128
TCP--R----- 192.168.1.55:3544 ttl 128
TCP--R----- 192.168.1.55:220 ttl 128
TCP--R----- 192.168.1.55:11201 ttl 128
TCP--R----- 192.168.1.55:7008 ttl 128
TCP--R----- 192.168.1.55:4000 ttl 128
TCP--R----- 192.168.1.55:6004 ttl 128
TCP--R----- 192.168.1.55:20012 ttl 128
TCP--R----- 192.168.1.55:6002 ttl 128
TCP--R----- 192.168.1.55:1433 ttl 128
TCP--R----- 192.168.1.55:1424 ttl 128
TCP--R----- 192.168.1.55:901 ttl 128
TCP--R----- 192.168.1.55:110 ttl 128
TCP--R----- 192.168.1.55:3232 ttl 128
TCP--R----- 192.168.1.55:1334 ttl 128
TCP--R----- 192.168.1.55:61466 ttl 128
TCP--R----- 192.168.1.55:58009 ttl 128
TCP--R----- 192.168.1.55:1352 ttl 128
TCP--R----- 192.168.1.55:2150 ttl 128
TCP--R----- 192.168.1.55:37 ttl 128
TCP--R----- 192.168.1.55:54320 ttl 128
TCP--R----- 192.168.1.55:7 ttl 128
TCP--R----- 192.168.1.55:59211 ttl 128
TCP--R----- 192.168.1.55:5355 ttl 128
TCP--R----- 192.168.1.55:443 ttl 128
listener statistics 418 packets recieved 0 packets droped and 0 interface drops
TCP--R----- echo[ 7] from 192.168.1.55 ttl 128
TCP--R----- discard[ 9] from 192.168.1.55 ttl 128
TCP--R----- daytime[ 13] from 192.168.1.55 ttl 128
TCP--R----- chargen[ 19] from 192.168.1.55 ttl 128
TCP open ftp[ 21] from 192.168.1.55 ttl 128
TCP--R----- ssh[ 22] from 192.168.1.55 ttl 128
TCP--R----- telnet[ 23] from 192.168.1.55 ttl 128
TCP--R----- smtp[ 25] from 192.168.1.55 ttl 128
TCP--R----- time[ 37] from 192.168.1.55 ttl 128
TCP--R----- tacacs[ 49] from 192.168.1.55 ttl 128
TCP--R----- re-mail-ck[ 50] from 192.168.1.55 ttl 128
TCP--R----- domain[ 53] from 192.168.1.55 ttl 128
TCP--R----- bootpc[ 68] from 192.168.1.55 ttl 128
TCP--R----- gopher[ 70] from 192.168.1.55 ttl 128
TCP--R----- finger[ 79] from 192.168.1.55 ttl 128
TCP--R----- http[ 80] from 192.168.1.55 ttl 128
TCP--R----- kerberos[ 88] from 192.168.1.55 ttl 128
TCP--R----- tacnews[ 98] from 192.168.1.55 ttl 128
TCP--R----- rtelnet[ 107] from 192.168.1.55 ttl 128
TCP--R----- pop2[ 109] from 192.168.1.55 ttl 128
TCP--R----- pop3[ 110] from 192.168.1.55 ttl 128
TCP--R----- sunrpc[ 111] from 192.168.1.55 ttl 128
TCP--R----- ident[ 113] from 192.168.1.55 ttl 128
TCP--R----- sqlserv[ 118] from 192.168.1.55 ttl 128
TCP--R----- ntp[ 123] from 192.168.1.55 ttl 128
TCP--R----- pwdgen[ 129] from 192.168.1.55 ttl 128
TCP--R----- netbios-dgm[ 138] from 192.168.1.55 ttl 128
TCP open netbios-ssn[ 139] from 192.168.1.55 ttl 128
TCP--R----- sql-net[ 150] from 192.168.1.55 ttl 128
TCP--R----- snmp[ 161] from 192.168.1.55 ttl 128
TCP--R----- snmptrap[ 162] from 192.168.1.55 ttl 128
TCP--R----- cmip-agent[ 164] from 192.168.1.55 ttl 128
TCP--R----- xdmcp[ 177] from 192.168.1.55 ttl 128
TCP--R----- prospero[ 191] from 192.168.1.55 ttl 128
TCP--R----- smux[ 199] from 192.168.1.55 ttl 128
TCP--R----- at-echo[ 204] from 192.168.1.55 ttl 128
TCP--R----- qmtp[ 209] from 192.168.1.55 ttl 128
TCP--R----- z39.50[ 210] from 192.168.1.55 ttl 128
TCP--R----- ipx[ 213] from 192.168.1.55 ttl 128
TCP--R----- imap3[ 220] from 192.168.1.55 ttl 128
TCP--R----- pawserv[ 345] from 192.168.1.55 ttl 128
TCP--R----- fatserv[ 347] from 192.168.1.55 ttl 128
TCP--R----- codaauth2[ 370] from 192.168.1.55 ttl 128
TCP--R----- clearcase[ 371] from 192.168.1.55 ttl 128
TCP--R----- ulistproc[ 372] from 192.168.1.55 ttl 128
TCP--R----- imsp[ 406] from 192.168.1.55 ttl 128
TCP--R----- timbuktu[ 407] from 192.168.1.55 ttl 128
TCP--R----- ariel3[ 422] from 192.168.1.55 ttl 128
TCP--R----- https[ 443] from 192.168.1.55 ttl 128
TCP--R----- snpp[ 444] from 192.168.1.55 ttl 128
TCP--R----- saft[ 487] from 192.168.1.55 ttl 128
TCP--R----- exec[ 512] from 192.168.1.55 ttl 128
TCP--R----- login[ 513] from 192.168.1.55 ttl 128
TCP--R----- ntalk[ 518] from 192.168.1.55 ttl 128
TCP--R----- efs[ 520] from 192.168.1.55 ttl 128
TCP--R----- timed[ 525] from 192.168.1.55 ttl 128
TCP--R----- netwall[ 533] from 192.168.1.55 ttl 128
TCP--R----- gdomap[ 538] from 192.168.1.55 ttl 128
TCP--R----- afpovertcp[ 548] from 192.168.1.55 ttl 128
TCP--R----- hmmp-ind[ 612] from 192.168.1.55 ttl 128
TCP--R----- ldaps[ 636] from 192.168.1.55 ttl 128
TCP--R----- esro-emsdp[ 642] from 192.168.1.55 ttl 128
TCP--R----- rmc[ 657] from 192.168.1.55 ttl 128
TCP--R----- mdqs[ 666] from 192.168.1.55 ttl 128
TCP--R----- pump[ 751] from 192.168.1.55 ttl 128
TCP--R----- webster[ 765] from 192.168.1.55 ttl 128
TCP--R----- rsync[ 873] from 192.168.1.55 ttl 128
TCP--R----- smpnameres[ 901] from 192.168.1.55 ttl 128
TCP--R----- unknown[ 923] from 192.168.1.55 ttl 128
TCP--R----- telnets[ 992] from 192.168.1.55 ttl 128
TCP--R----- pop3s[ 995] from 192.168.1.55 ttl 128
TCP--R----- reserved[ 1024] from 192.168.1.55 ttl 128
TCP--R----- blackjack[ 1025] from 192.168.1.55 ttl 128
TCP--R----- cap[ 1026] from 192.168.1.55 ttl 128
TCP open exosee[ 1027] from 192.168.1.55 ttl 128
TCP--R----- unknown[ 1028] from 192.168.1.55 ttl 128
TCP--R----- socks[ 1080] from 192.168.1.55 ttl 128
TCP--R----- eoss[ 1210] from 192.168.1.55 ttl 128
TCP--R----- search-agent[ 1234] from 192.168.1.55 ttl 128
TCP--R----- writesrv[ 1334] from 192.168.1.55 ttl 128
TCP--R----- sbook[ 1349] from 192.168.1.55 ttl 128
TCP--R----- lotusnote[ 1352] from 192.168.1.55 ttl 128
TCP--R----- hybrid[ 1424] from 192.168.1.55 ttl 128
TCP--R----- ms-sql-s[ 1433] from 192.168.1.55 ttl 128
TCP--R----- ms-sql-m[ 1434] from 192.168.1.55 ttl 128
TCP--R----- ingreslock[ 1524] from 192.168.1.55 ttl 128
TCP--R----- orasrv[ 1525] from 192.168.1.55 ttl 128
TCP--R----- sightline[ 1645] from 192.168.1.55 ttl 128
TCP--R----- sa-msg-port[ 1646] from 192.168.1.55 ttl 128
TCP--R----- l2f[ 1701] from 192.168.1.55 ttl 128
TCP--R----- h323gatedisc[ 1718] from 192.168.1.55 ttl 128
TCP--R----- h323hostcall[ 1720] from 192.168.1.55 ttl 128
TCP--R----- ms-streaming[ 1755] from 192.168.1.55 ttl 128
TCP--R----- radius[ 1812] from 192.168.1.55 ttl 128
TCP--R----- dls-monitor[ 2048] from 192.168.1.55 ttl 128
TCP--R----- av-emb-config[ 2050] from 192.168.1.55 ttl 128
TCP--R----- rtcm-sc104[ 2101] from 192.168.1.55 ttl 128
TCP--R----- zephyr-clt[ 2103] from 192.168.1.55 ttl 128
TCP--R----- ias-reg[ 2140] from 192.168.1.55 ttl 128
TCP--R----- dynamic3d[ 2150] from 192.168.1.55 ttl 128
TCP--R----- infocrypt[ 2233] from 192.168.1.55 ttl 128
TCP--R----- dbm[ 2345] from 192.168.1.55 ttl 128
TCP--R----- cvspserver[ 2401] from 192.168.1.55 ttl 128
TCP--R----- venus[ 2430] from 192.168.1.55 ttl 128
TCP--R----- codasrv[ 2432] from 192.168.1.55 ttl 128
TCP--R----- mon[ 2583] from 192.168.1.55 ttl 128
TCP--R----- dict[ 2628] from 192.168.1.55 ttl 128
TCP--R----- ridgeway1[ 2776] from 192.168.1.55 ttl 128
TCP--R----- icpv2[ 3130] from 192.168.1.55 ttl 128
TCP--R----- nm-asses-admin[ 3150] from 192.168.1.55 ttl 128
TCP--R----- mdtp[ 3232] from 192.168.1.55 ttl 128
TCP--R----- mysql[ 3306] from 192.168.1.55 ttl 128
TCP--R----- ms-wbt-server[ 3389] from 192.168.1.55 ttl 128
TCP--R----- qftest-lookup[ 3543] from 192.168.1.55 ttl 128
TCP--R----- teredo[ 3544] from 192.168.1.55 ttl 128
TCP--R----- unknown[ 3801] from 192.168.1.55 ttl 128
TCP--R----- terabase[ 4000] from 192.168.1.55 ttl 128
TCP--R----- radmin-port[ 4899] from 192.168.1.55 ttl 128
TCP--R----- rfe[ 5002] from 192.168.1.55 ttl 128
TCP--R----- unknown[ 5136] from 192.168.1.55 ttl 128
TCP--R----- ctsd[ 5137] from 192.168.1.55 ttl 128
TCP--R----- unknown[ 5138] from 192.168.1.55 ttl 128
TCP--R----- unknown[ 5139] from 192.168.1.55 ttl 128
TCP--R----- xmpp-client[ 5222] from 192.168.1.55 ttl 128
TCP--R----- cfengine[ 5308] from 192.168.1.55 ttl 128
TCP--R----- llmnr[ 5355] from 192.168.1.55 ttl 128
TCP--R----- salient-mux[ 5422] from 192.168.1.55 ttl 128
TCP--R----- virtualuser[ 5423] from 192.168.1.55 ttl 128
TCP--R----- unknown[ 5425] from 192.168.1.55 ttl 128
TCP--R----- rplay[ 5555] from 192.168.1.55 ttl 128
TCP--R----- rplay[ 5556] from 192.168.1.55 ttl 128
TCP--R----- x11[ 6000] from 192.168.1.55 ttl 128
TCP--R----- unknown[ 6001] from 192.168.1.55 ttl 128
TCP--R----- unknown[ 6002] from 192.168.1.55 ttl 128
TCP--R----- unknown[ 6004] from 192.168.1.55 ttl 128
TCP--R----- unknown[ 6005] from 192.168.1.55 ttl 128
TCP--R----- unknown[ 6006] from 192.168.1.55 ttl 128
TCP--R----- unknown[ 6007] from 192.168.1.55 ttl 128
TCP--R----- gnutella-svc[ 6346] from 192.168.1.55 ttl 128
TCP--R----- gnutella-rtr[ 6347] from 192.168.1.55 ttl 128
TCP--R----- lds-distrib[ 6543] from 192.168.1.55 ttl 128
TCP--R----- unknown[ 6544] from 192.168.1.55 ttl 128
TCP--R----- irc[ 6667] from 192.168.1.55 ttl 128
TCP--R----- irc[ 6668] from 192.168.1.55 ttl 128
TCP--R----- irc[ 6669] from 192.168.1.55 ttl 128
TCP--R----- vocaltec-gold[ 6670] from 192.168.1.55 ttl 128
TCP--R----- smc-https[ 6789] from 192.168.1.55 ttl 128
TCP--R----- afs3-fileserver[ 7000] from 192.168.1.55 ttl 128
TCP--R----- afs3-callback[ 7001] from 192.168.1.55 ttl 128
TCP--R----- afs3-prserver[ 7002] from 192.168.1.55 ttl 128
TCP--R----- afs3-volser[ 7005] from 192.168.1.55 ttl 128
TCP--R----- afs3-bos[ 7007] from 192.168.1.55 ttl 128
TCP--R----- afs3-update[ 7008] from 192.168.1.55 ttl 128
TCP--R----- unknown[ 7983] from 192.168.1.55 ttl 128
TCP open unknown[ 8081] from 192.168.1.55 ttl 128
TCP--R----- radan-http[ 8088] from 192.168.1.55 ttl 128
TCP--R----- msgsrvr[ 8787] from 192.168.1.55 ttl 128
TCP--R----- unknown[ 8879] from 192.168.1.55 ttl 128
TCP--R----- websm[ 9090] from 192.168.1.55 ttl 128
TCP--R----- bacula-dir[ 9101] from 192.168.1.55 ttl 128
TCP--R----- bacula-fd[ 9102] from 192.168.1.55 ttl 128
TCP--R----- bacula-sd[ 9103] from 192.168.1.55 ttl 128
TCP--R----- unknown[ 9325] from 192.168.1.55 ttl 128
TCP--R----- unknown[ 9359] from 192.168.1.55 ttl 128
TCP--R----- unknown[10027] from 192.168.1.55 ttl 128
TCP--R----- unknown[10067] from 192.168.1.55 ttl 128
TCP--R----- amanda[10080] from 192.168.1.55 ttl 128
TCP--R----- unknown[10081] from 192.168.1.55 ttl 128
TCP--R----- unknown[10167] from 192.168.1.55 ttl 128
TCP--R----- smsqp[11201] from 192.168.1.55 ttl 128
TCP--R----- unknown[17002] from 192.168.1.55 ttl 128
TCP--R----- unknown[17003] from 192.168.1.55 ttl 128
TCP--R----- unknown[20012] from 192.168.1.55 ttl 128
TCP--R----- wnn6[22273] from 192.168.1.55 ttl 128
TCP--R----- unknown[26274] from 192.168.1.55 ttl 128
TCP--R----- unknown[31336] from 192.168.1.55 ttl 128
TCP--R----- unknown[31789] from 192.168.1.55 ttl 128
TCP--R----- unknown[31790] from 192.168.1.55 ttl 128
TCP--R----- unknown[31791] from 192.168.1.55 ttl 128
TCP--R----- unknown[32668] from 192.168.1.55 ttl 128
TCP--R----- unknown[32767] from 192.168.1.55 ttl 128
TCP--R----- filenet-tms[32768] from 192.168.1.55 ttl 128
TCP--R----- filenet-rpc[32769] from 192.168.1.55 ttl 128
TCP--R----- filenet-nch[32770] from 192.168.1.55 ttl 128
TCP--R----- filenet-rmi[32771] from 192.168.1.55 ttl 128
TCP--R----- filenet-cm[32773] from 192.168.1.55 ttl 128
TCP--R----- filenet-re[32774] from 192.168.1.55 ttl 128
TCP--R----- unknown[32776] from 192.168.1.55 ttl 128
TCP--R----- unknown[47262] from 192.168.1.55 ttl 128
TCP--R----- unknown[49301] from 192.168.1.55 ttl 128
TCP--R----- unknown[54320] from 192.168.1.55 ttl 128
TCP--R----- unknown[54321] from 192.168.1.55 ttl 128
TCP--R----- unknown[58008] from 192.168.1.55 ttl 128
TCP--R----- unknown[58009] from 192.168.1.55 ttl 128
TCP--R----- unknown[58666] from 192.168.1.55 ttl 128
TCP--R----- unknown[59211] from 192.168.1.55 ttl 128
TCP--R----- unknown[60000] from 192.168.1.55 ttl 128
TCP--R----- unknown[60006] from 192.168.1.55 ttl 128
TCP--R----- unknown[61000] from 192.168.1.55 ttl 128
TCP--R----- unknown[61466] from 192.168.1.55 ttl 128
TCP--R----- unknown[61603] from 192.168.1.55 ttl 128
TCP--R----- unknown[63485] from 192.168.1.55 ttl 128
TCP--R----- unknown[63809] from 192.168.1.55 ttl 128
TCP--R----- unknown[64429] from 192.168.1.55 ttl 128
TCP--R----- unknown[65000] from 192.168.1.55 ttl 128
TCP--R----- unknown[65506] from 192.168.1.55 ttl 128
TCP--R----- unknown[65532] from 192.168.1.55 ttl 128
TCP--R----- unknown[65533] from 192.168.1.55 ttl 128
TCP--R----- unknown[65534] from 192.168.1.55 ttl 128
main exiting
The results that certain ports are open and most of them having the R bit which is reset bit. This is a window server, by looking the ttl, i can easily enumerate that it is a windows machine. Different servers have different ttl values and ttl 128 belongs to the windows group. Of course you can change it in the registry, but most people leave it default. Search for ttl values for cisco in google, you might find some interesting stuffs.
I will be busy pentesting a telco for the next few days, so maybe less updates. But well, i will try to get back on track soon with more commands. Meanwhile, i am going to use Rsnake's fierce for my project.